The hacking of digital wallets and other forms of digital theft are major problems for people and organizations who engage in cryptocurrency trading. The market for cryptocurrencies has attracted the attention of both genuine investors and unethical hackers as a consequence of the incredible spike in value that has occurred over the years. Through this blog, we are going to tell you how to prevent cryptocurrency from fraud or being hacked. We’ll also share a wallet name which is the most secure crypto wallet to store your cryptocurrency.
Table of Contents
Fundamentals of Crypto Security
Blockchain technology is the primary system which protects cryptocurrencies from any kind of fraud and cyber threats. Blockchain uses two types of cryptography to ensure the security of cryptocurrencies and other information: hash functions and public key cryptography. The purpose of hash functions is to ensure that no one can change the data that is stored on a blockchain without the modifications being noticed. This is accomplished by preventing unauthorized users from making modifications to the data. This accomplishes its goal by making it very hard to identify two versions of the data that, when hashed, create the same output value. This is done by ensuring that the output value produced by hashing the data is unique.
1. Cryptography: The Backbone of Crypto Security
The use of codes in cryptography is a technique for securing information and communications, with the goal of ensuring that only the individuals who are intended to read and use the information can comprehend and act upon it. Consequently prohibiting access to information by unauthorized parties. Mathematical principles and a system of rule-based computations known as algorithms are used in cryptography to change messages in a way that makes it difficult to decode the information they conceal. The procedures that are used to protect information are derived from these mathematical principles. These algorithms are used for the production of cryptographic keys, digital signing, and verification in order to secure data privacy, online browsing on the internet, and secret transactions such as those involving credit cards and debit cards.
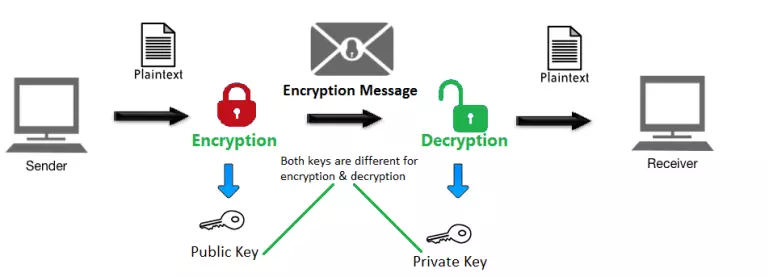
2. Public and Private Keys: Building Blocks of Protection
In cryptography, Private Keys and Public Keys general terms are used for security purposes. These keys help to encrypt/decrypt important or sensitive data. Public keys are only used to encrypt sensitive information. The sender and the recipient are the only people who have access to each other’s private keys, but public keys can be freely shared with a number of different users.
3. Wallet Types: Exploring Different Security Options
Wallets are the devices which help the asset or fund holder to keep them in a protected place without any worries. Blockchain wallets are the most reliable ones as they provide top-level security. The security of blockchain makes the process less hectic for the users to do crypto transactions and other operations. There are several wallets available in the market, some of which are:
1. Hardware Wallets: Maximum Security for Your Assets
Hardware wallets are the only ones that truly express the ideas behind the construction of a cold wallet. They provide security by preventing the online disclosure of private keys in every way possible. Hardware wallets operate in the same manner as flash drives and store private keys on a physical device that is stored in an offline environment. Hardware wallets are one of the easiest types of cold wallets to use because you can easily connect them to computers or any other device with a USB drive.
2. Software Wallets: Balancing Convenience and Safety
The term “software wallet” refers to a piece of software that may be downloaded and installed on a user’s own computer. Although it could give the impression that you keep your coins on your computer, this is not actually the case. The vast majority of software wallets give users the ability to store more than one cryptocurrency, and some wallets even include exchange services that let users trade one cryptocurrency for another without having to exit the wallet’s UI.
3. Paper Wallets: Offline Storage for Enhanced Security
When it comes to understanding paper wallets as one of the sorts of cryptocurrency wallets, the name gives a lot away about what they are and how they work. Paper wallets are literally just pieces of paper that you carry around with you. The piece of paper must include all of the information that is necessary to gain access to digital currencies. In most cases, cold wallets provide an additional layer of security.
Check Out: Top 10 Best Crypto Wallets in India
How To Avoid Getting Hacked?
Avoiding getting hacked is essential in today’s digital age, where cyber threats are becoming increasingly prevalent. Here are some tips to help you protect yourself from being hacked.
Create unique, complex passwords for all your online or crypto wallet accounts and change them regularly. It is highly recommended that you should avoid using the same password for several accounts. Two-factor authentication adds an extra layer of security by requiring a second form of verification, such as a text message or fingerprint, to log in to your accounts.

Don’t click on links or download attachments from suspicious emails, even if they appear to be from a legitimate source. Keep your operating system, applications, and antivirus software up to date with the latest security patches and updates to reduce the risk of vulnerabilities being exploited. By encrypting your internet connection and masking your IP address, a virtual private network (VPN) may make your online activities more secure.
It is best to stay away from entering private information, such as your bank account, while using public Wi-Fi networks. Hackers can easily intercept data on these networks. Be cautious about the information you share on social media, as it can be used by hackers to gain access to your accounts or steal your identity.
Also Check: Is Cryptocurrency Truly the Future of Money?
Best Practices for Securing Your Crypto
Preventing fraud and hacking in the world of cryptocurrencies can be challenging, but there are several measures you can take to reduce the risk:
1. Use a reputable cryptocurrency exchange
You should do some research on the exchange or platform you want to use and make sure it has a strong reputation in terms of both its security and its customer care.
2. Enable two-factor authentication (2FA)
If you enable two-factor authentication (2FA), you will add a layer of protection to your account, making it far more difficult for malicious actors to access it.
3. Use a strong password
When establishing a secure and unique password for your cryptocurrency accounts, it is recommended that you use a mixture of uppercase and lowercase letters, digits, and special characters.
4. Keep your private keys offline
If you keep your private keys offline, for example in a hardware wallet or some other kind of safe storage, you can reduce the risk of hackers stealing them.
5. Be cautious of phishing scams
Scammers may send you phishing emails or create bogus websites in an attempt to get you to hand over vital information or private keys so that they may steal your identity. Before providing any personal information, you should exercise extreme caution and always confirm the legitimacy of the website or email.
6. Keep your software up to date
To reduce the probability of security flaws being exploited, you should ensure that all cryptocurrency-related applications on your computer, as well as any other software that uses cryptocurrency, have the most recent security patches and updates installed.
7. Don’t share your personal information
Never provide anyone access to your personal information or login credentials since doing so might leave you open to identity theft and other forms of cybercrime.
By taking these steps and staying informed about the latest security threats, you can help reduce the risk of fraud and hacking in the world of cryptocurrencies.
Most secure crypto wallet- Funex Wallet
When it comes to storing crypto, the Funex wallet is one of the best options available. It’s user-friendly, and it contains a lot of safety options. It’s a great cryptocurrency wallet that supports Ethereum and Bitcoin. According to Funex users, it is the best multi-crypto wallet The customer service staff will reply immediately to help you discover a solution if you’re still having problems.
Funex cryptocurrency wallet is a secure wallet for Bitcoin, Ethereum, Tron, Binance, Funex, and more. It is the best crypto wallet for storing multiple cryptocurrencies at a time. If you’re looking for the most secure Ethereum wallet, go no further than this top custodian or centralized wallet. The best cryptocurrency wallet application for security and speed. This custodial wallet is fantastic for storing digital assets and NFTs as well. Compared to other cryptocurrency wallets, this one performs better.
Conclusion
Cryptocurrencies have revolutionized the financial landscape, offering exciting opportunities for investors and users. However, with great potential comes significant responsibility. Safeguarding your digital assets from fraud and hacking is essential to protect your hard-earned investments. In this blog, we will explore practical and proactive measures to enhance the security of your cryptocurrencies and mitigate potential risks.
As the cryptocurrency market continues to grow, it is vital to remain vigilant and proactive in safeguarding your digital assets. By following these best practices and staying informed about the evolving security landscape, you can minimize the risk of fraud and hacking. Remember, protecting your cryptocurrencies is an ongoing process, and prioritizing security will ensure a safer and more rewarding crypto journey. Funex wallet is a reliable crypto wallet to store your cryptocurrencies safely and securely.
FAQs
Q1. What is the most secure type of wallet for storing crypto?
While selecting the best and secure crypto wallet, one should evaluate their needs. However, blockhain wallets are the most secure and can store multiple cryptocurrencies with any amount for a long time. A blockchain wallet is a safe option to manage, store, do transactions and spend your cryptocurrency.
Q2. How can I protect my crypto from SIM card swaps?
Protecting your crypto from SIM card swaps is crucial to prevent unauthorized access to your accounts and funds. Contact your mobile service provider and set up a PIN or passcode on your SIM card and avoid using SMS-based 2FA for your crypto accounts. Be cautious about sharing personal information, such as your phone number or account details, online or with unknown individuals.
Q3. Are there any insurance options for safeguarding crypto?
Yes, as the demand for cryptocurrencies continues to grow, a growing number of companies are beginning to offer insurance policies. Crypto insurance provides protection against financial losses resulting from breaches in cybersecurity, such as theft or hacking.
Q4. What should I do if I suspect my crypto has been compromised?
If you suspect that your cryptocurrency has been compromised, Change all passwords and enable two-factor authentication (2FA) on all your crypto exchange and wallet accounts. Immediately contact the customer support of the affected crypto exchange or wallet provider to report the issue. If possible, freeze your accounts or assets to prevent further unauthorized access.



